Twitter #Hacked
- By Ceecee Wong
- July 20, 2020
Last week’s Twitter hack was the largest social media hack in recent memory, which compromised over 130 accounts, according to the social media giant.
The hack involved many high-profile and verified Twitter accounts such as those belonging to Bill Gates, Elon Musk, Joe Biden, Barack Obama, Kanye West, Apple, Uber and many more, tweeting out bitcoin scams that promised to ‘give back’ to their communities.
“[It is] worrying that high-profile accounts could be compromised with no alarm bells ringing at the office,” said Amar Singh, chief executive officer and trusted advisor in cybersecurity and privacy at Cyber Management Alliance Ltd.
So, where were the alarm bells?
The tweets themselves used a common scamming technique where people were asked to send out funds to get a return of bigger amounts, or in this case ‘doubled’ amounts.
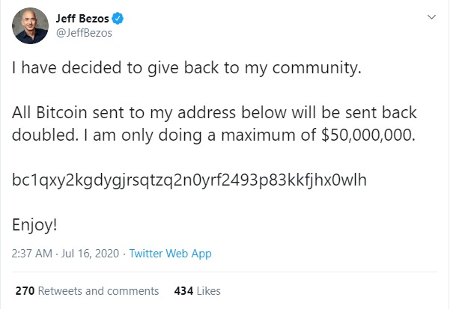
Some feel that it may not be as simple as it sounds.
“After initially looking like successful social engineering of some key insiders, there is some talk that ‘traditional’ methods were used to buy inside cooperation and access to the admin tool that allowed the takeover of high profile accounts. Either way, it shows that hackers will always target the privileged access and rights of insiders,” said Jeffrey Kok, vice president for solution engineers in Asia Pacific and Japan at CyberArk.
No matter the complexity (or simplicity), what is surprising is not the hack itself but how long it took for Twitter to address it.
“The lesson companies should take away from this: Ask themselves if they are prepared to respond to an attack. Do they have early-warning alarm bells configured to warn them about successful attacks before the final act of destruction is completed?” said Singh.
The crypto undertones
While involving famous figures that span tech, politics and entertainment circles, the Twitter hack had undeniable crypto overtones. Besides the obvious fact that solicitations were via BTC, the hack targeted prominent crypto exchanges and individuals first.
The company accounts of crypto exchanges Binance and Coinbase and then the individual account of Binance CEO Changpeng Zhao were hacked first, followed by other well-known organizations and individuals in the crypto community, hours before the accounts of the luminaries in the other various spheres of influence were affected.
Paul Ducklin, Principal Research Scientist at Sophos, warned that “if a message sounds too good to be true, it is too good to be true.”
He also sounded alarm bells for “cryptocurrency transactions that don't have the legal protections that you get with banks or payment card companies.”
Ducklin cautioned that in the world of cryptocurrencies, there was “no fraud reporting service or transaction cancellation”, comparing handing over crypto to handing over cash to a stranger in an envelope.
But don’t blame the crypto exchanges
Hours after the hack occurred, Binance chief executive officer Changpeng Zhao (known as CZ), the first individual hacked, spoke at World Blockchain Summit Asia 2020, about the massive global social media hack.
Originally believing the attack to be a problem “on our side as we’re constantly under attack on our Twitter accounts”, CZ realized the problem originated from Twitter when other accounts were attacked, commenting that Twitter offered “limited security options” and that those options available were “a little weak”.
Calling the attempt “amateurish”, CZ nevertheless exhorted the entire industry to be vigilant:
“I do want to encourage the industry to actively block and blacklist those [BTC] addresses [used in the hack]. This is not centralization, we need to fight against the bad actors… I don’t think people lost a lot of money on this one, so it actually [works as] a good wakeup call for the whole industry to be more vigilant when it comes to security.”
On Binance’s part, all the addresses were blacklisted within the hour, steps were taken to ensure that there were no funds going out from Binance user accounts and lastly, the exchange reached out to their partners in the crypto space to do the same.
When Joon Ian Wong, managing director of Coindesk (a crypto editorial whose account was also hacked on Twitter) asked if this was the first time that exchanges had collaborated to blacklist a certain set of addresses, CZ had a reassuring answer: “No, we actually do have communication channels amongst different exchanges, for this particular purpose. So if one exchange gets hacked, the other exchanges always step in to help... Exchanges do compete on the business level, but for fighting fraud we actually work together quite collaboratively. Doing that helps the entire industry. There are a large number of exchanges who are very collaborative in this regard... If we asked them to freeze suspicious funds or vice versa, we will all absolutely comply.”
Lawmakers instead blame Twitter
In his open letter to Twitter chief executive office Jack Dorsey, Senator Josh Hawley expressed concern that “this event may represent not merely a coordinated set of separate hacking incidents but rather a successful attack on the security of Twitter itself.”
Noting that millions of users relied on the service not just to tweet publicly but also to communicate privately through direct messaging, a successful attack on Twitter’s system servers “represents a threat to all users’ privacy and data security.”
In a statement to Business Insider, Senator Ron Wyden threw shade on Twitter’s DM (direct messaging) architecture, pointing out that it lacked end-to-end encryption: “This is a vulnerability that has lasted for far too long, and one that is not present in other, competing platforms. If hackers gained access to users’ DMs, this breach could have a breathtaking impact for years to come.”
CyberArk’s Kok is less surprised. “We have seen how hackers could target high-profile individuals by hijacking an administrator tool.”
He advised companies to proactively manage and rotate high-value “privileged” credentials, and limit user access to only the information and tools needed to perform their immediate role. This can stop “an attacker’s route to critical data and assets… This reduces their ability to exfiltrate, manipulate information or disrupt operations.”
Impact on crypto is muted
So amid all this global controversy, how is Bitcoin holding up in the markets?
The markets seem to show that the hack has been a bit of a non-event for the cryptocurrency itself. Right after the hack, BTC slid about 0.8% to USD 9,100 on Thursday, considered insignificant for a spectacularly volatile cryptocurrency where 8% daily price swings are not at all uncommon. As of this writing BTC is currently at USD 9,200.
In fact, all publicity is still good publicity for the crypto cause, not having reached massive levels of adoption yet. The fact that such an attention-grabbing, sensational scam involved criminals requesting Bitcoin and not cash, has inadvertently put a spotlight on the value of Bitcoin. The hack has also shown how easy it is to track stolen crypto.
While there is no central bank to oversee transactions, the overarching factor in Bitcoin’s favor is that the ledger of all Bitcoin transactions is public and searchable. This means that it is entirely possible to trace the source, movement and destination of the funds, from wallets to exchanges, the destination where BTC can be cashed out.
If the entire crypto exchange community is as collaborative as CZ has reassured us to be, it should be a matter of time before their concerted efforts will lead us to tracking down criminals and hopefully, de-incentivize future hacking attempts.
Impact on social media security is pronounced
The biggest impact will be on how companies will view their social media exposure.
“The interconnectivity of social media and the inherent trust that people have in it makes it a powerful vehicle. As we’ve seen multiple times before, social media can be successfully weaponized by attackers seeking financial gain or disruption,” said Kok.
He noted that it is “becoming more apparent than ever” that these social media platforms need to be considered critical infrastructure and protected accordingly. Every CEO must question what their most valuable assets are, who has access, and how that access is being monitored and protected — even if it is just a Twitter account.
Whatever the reason that Twitter overlooked the security posture, this is only the start. Having tasted some success, you can bet that social media will be the new flavor of attack vectors in the coming weeks.
Beware of your next Tweet.
Additional reporting by Winston Thomas
Photo credit: iStockphoto/TanyaMcClure









